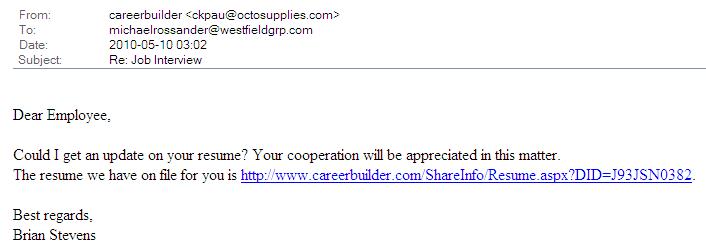
Several coworkers and I got the same scam email this morning. The message body is attached below. It’s sneaky in its simplicity. There is so little content that the spam filters have nothing to work with – there’s little that a computer can use to differentiate this from a thousand similar but legitimate business emails.
There are a few clues for you as a human reader to look for, however.
- The greeting line is generic – “Dear Employee” rather than “Dear Mike” or “Mr. Rossander”.
- The From address is an odd or at least a non-corporate address (redbran@galleryfifty4.com).
- The link is spoofed. That is, it appears to point to a legitimate careerbuilder.com page but when you float over the link (or right-click and look at properties), it is actually pointing to swc.com.ua/resume.pdf.
- The spoofed address is in the Ukraine (the .ua part of the address). Careerbuilder is an international company but to the best of my knowledge, they do not have any servers there. And none likely to be handling english-speaking matters.
- Do you even have an account with Careerbuilder? They are a legitimate company and I did have a resume on file with them once but several of my coworkers did not. The age since my last contact with the company was a clue for me – the complete lack of prior relationship a better clue for my coworkers.
Unfortunately, there is no guaranteed way to block these scams. The best we can do is delete them and move on with your day. In the meantime, remember that it’s not paranoia when they really are out to get you.

