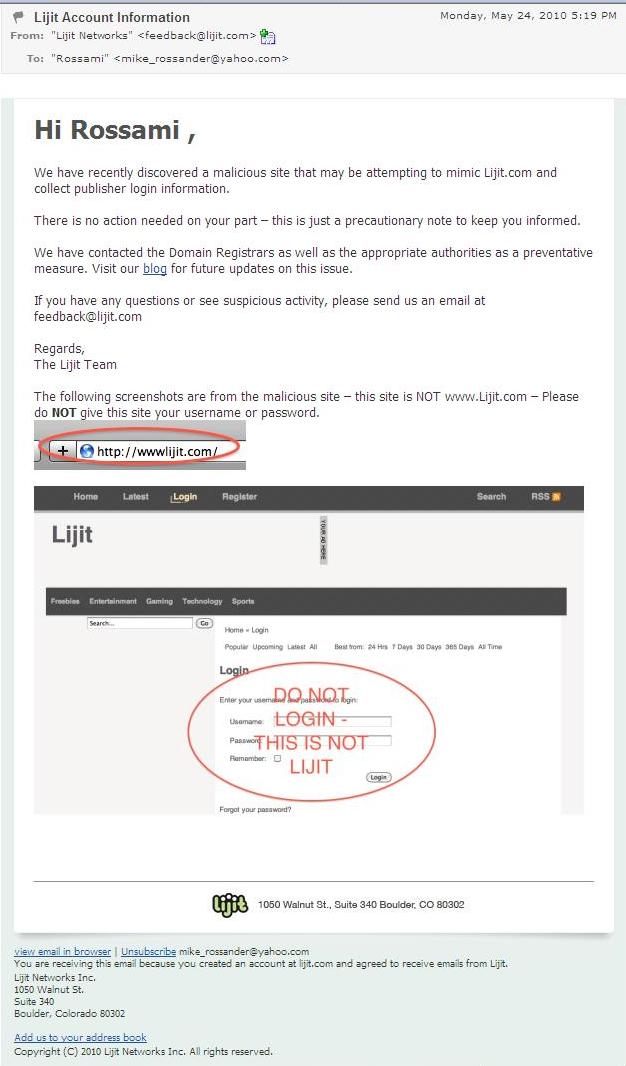
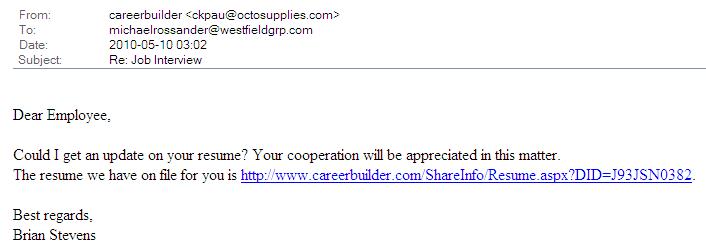
It’s an interesting morning. I received three spam messages in rapid succession, each alleging to come from “NSA online security” and reporting a “critical vulnerability” in “a certain types of our token devices.” While I don’t expect perfect grammar from a government functionary, the mistakes in this email were pretty obvious. The alleged link to “fix” the problem point to “national-security-agency.com” which looks pretty plausible until you remember (or look up) that the real NSA uses the domain nsa.gov.
What’s interesting about this case is that it’s a fairly blatant example of an attempt to turn your computer into a zombie using the ZeuS Command&Control attack. If I had been stupid enough to click the link, I would have launched an executable program that would log every keystroke that I make on the machine and that would grab a copy of every form I fill out online. Since that would include my online banking login page, it would have given the hacker access to all my banking information.
ZeuS is a moderately old Trojan Horse but it is remarkably difficult for anti-virus programs to detect, even when kept completely up-to-date. ZeuS is alleged to be one of the largest botnets in the world, infecting some 3.6 million computers in the US alone.
The continued success of attacks like this show why you can never rely only on your anti-virus software. Read your email carefully, be suspicious and never click a link if you’re not sure that it’s safe to do so. Remember – it’s not paranoia when they really are out to get you.